- Docs>
- Kakao Login>
- Webhook
menu
Getting started
Kakao Developers
Login
Communication
Advertisement
- Concepts
- Ad creation: Ad account
- Ad creation: Campaign
- Ad creation: Ad group
- Targeting for ad group
- Custom audience targeting for ad group
- Ad creation: Creative common
- Ad creation: Display creative
- Ad creation: Message creative
- Ad creation: Personalized message creative
- Bizboard landing settings
- Report
- Message management
- Personalized message management
- Message ad management
- Message ad operation
- Ad View management
- Business Form linkage management
- Pixel & SDK linkage management
- Audience management
- Engagement targeting management
- Customer file management
- Friend group management
- Ad account management
- Reference
- Type information
- Error code
Kakao Login


Webhook
This document introduces webhook system for Kakao Login.
Webhook is a feature that sends an HTTP request to the webhook URL set in Kakao Developer to share with the service when there is a change in the account status of a Kakao Login user.
The webhook system is designed based on the Shared Signals and Events Framework(SSF) developed by the OpenID Foundation, with additional event types specifically defined by Kakao.
Before you begin
This document explains the webhook requests that Kakao sends to your service's endpoint. Note that this specification describes incoming webhook requests from Kakao, not API requests that your service makes to Kakao.
For the overall workflow and detailed implementation guide for webhooks, see Implementation steps.
Unlink webhook
Basic information
| Method | URL | Required response | Authorization |
|---|---|---|---|
GET/POST |
Webhook URL registered in [App] > [Webhook] on the app management page | HTTP status code 200 OK (within 3 seconds) |
Primary admin key |
| Permission | Prerequisite | Kakao Login | User consent |
|---|---|---|---|
| - | Admin key Activate Kakao Login Set unlink webhook |
- | - |
The unlink webhook is a feature where Kakao notifies the service when a user disconnects the app outside the service. Upon receiving the webhook, the service must process the user's information according to its internal policy and respond with an HTTP status code 200 OK within 3 seconds.
Users who request to unlink outside the service will see a message that the service is no longer available. The unlink webhook is sent after completing the unlink process for the user.
The webhook includes the Service app admin key in the header, and app ID (app_id), user ID (user_id), unlink request source (referrer_type) in the body.
Prerequisites
The unlink webhook requires specifying a webhook URL and method, and redirection is not supported. For configuration details, refer to Set unlink webhook.
Conditions for sending unlink webhooks
Unlink webhooks are sent under the following conditions. However, if the service calls the Unlink API to disconnect the app from the user, the unlink webhook will not be sent.
- Unlinking users who have not completed registration.
- When a user disconnects the app via the Kakao Account management page or the Unlink on Manage connected services menu in Kakao Talk.
- When the user deletes their Kakao Account.
- When the app is unlinked due to a customer service request.
Actions upon receiving a webhook
The service must respond according to the specified format after perform the necessary tasks upon receiving a webhook. Refer to the steps below.
- Verify the received webhook using the included Service app admin key and
app_id. - If the webhook is valid, process the user information corresponding to
user_idin the database (DB) by performing deletion, removal, or other actions in accordance with the privacy policy and service policy. - Respond with an HTTP status code
200 OKwithin 3 seconds of receiving the webhook.- No body content is required because the success of the response is determined by the HTTP status code.
- Even if user information processing fails or the user cannot be found, respond with an HTTP status code
200 OK. Perform any additional necessary tasks internally within the service afterward.
Testing the unlink webhook
To receive an unlink webhook, simulate a scenario where the user disconnects the app. The unlink feature is available on the Kakao Account page or in Kakao Talk via [More] > [Settings] > [Kakao Account]. Use this feature to verify whether the service server processes unlink webhooks correctly.
Request
Header
| Name | Description | Required |
|---|---|---|
| Authorization | String |
Authorization: KakaoAK ${SERVICE_APP_ADMIN_KEY}The Admin key as a type of user authentication. |
Parameter
| Name | Type | Description | Required |
|---|---|---|---|
| app_id | String |
App ID that a user requests to unlink from. | O |
| user_id | String |
Service user ID of a user who requests to unlink. | O |
| referrer_type | String |
The route of a user requests to unlink. One of the followings: - ACCOUNT_DELETE: If a user deletes the Kakao Account. - FORCED_ACCOUNT_DELETE: If a user's Kakao Account is deleted through Customer Service or deleted after a four-year dormant state. - UNLINK_FROM_APPS: If a user selects [Disconnect] on 'Manage Connected Services'. - UNLINK_FROM_ADMIN: If a user requests to unlink through the Kakao Customer service. - INCOMPLETE_SIGN_UP: If a user has not completed a signup. (Refer to Notice) |
O |
| group_user_token | String |
Group user token of the user who requested to unlink, provided only when the unlink occurs in a group app | X |
Response
You must respond with HTTP status code 200 OK within 3 seconds of receiving the webhook request.
Sample
Theses are examples of the webhook request that Kakao sends to your service when a user unlinks outside of the service.
Request: GET method
curl -v -G GET "{UNLINK_CALLBACK_URL}?app_id=123456&user_id=1234567890&referrer_type=UNLINK_FROM_APPS" \
-H "Authorization: KakaoAK ${SERVICE_APP_ADMIN_KEY}"
Request: POST method
curl -v -X POST "{UNLINK_CALLBACK_URL}" \
-H "Authorization: KakaoAK ${SERVICE_APP_ADMIN_KEY}" \
--data-urlencode "app_id=123456" \
--data-urlencode "user_id=1234567890" \
--data-urlencode "referrer_type=UNLINK_FROM_APPS"
Response
This is an example of the response your service endpoint should send to Kakao.
HTTP/1.1 200 OK
Account status change webhook
Basic information
| Method | URL | Required response format | Authentication |
|---|---|---|---|
POST |
Webhook URL registered in [My Applications] > [Kakao Login] > [Account Status Change Webhook] | Respond within 3 seconds based on the SET verification results: - Success: HTTP status code 202 Accepted- Failure: HTTP status code 400 Bad Request with specified header and body (Reference) |
Primary REST API key |
| Permission | Prerequisite | Kakao Login | User consent |
|---|---|---|---|
| - | REST API key Activate Kakao Login Account status change webhook |
Required | Required to use the events in CAEP, RISC category |
The account status change webhook sends event information to the specified webhook URL whenever a user's account status changes.
For implementation steps, refer to Implementation steps.
Your service must respond to webhook requests with either a success or a validation failure response as specified. If no response is received or the response does not comply with the validation failure format, Kakao considers the event delivery as failed and attempts a retry. Continuous delivery failures may result in webhook deactivation.
How to use
- Review the information you want to receive. Some event categories require Consent item settings. See Supported Event Types.
- Configure the webhook URL and select event types. See Prerequisites.
- Implement the functionality to validate and process the SET received through the webhook URL by referring to Validate SET.
- Implement the necessary actions by referring to the Recommended actions column in the Event Types table.
- To check the specifications of the Account status change webhook system, see Get metadata (Optional).
- To test how webhooks are sent, see Test (Optional).
Set Consent items
Change events under the CAEP and RISC categories may include sensitive information. Thus, these require configuring the [Kakao Account status change details] consent item and obtaining user consent.
If necessary, follow the steps below:
- Request for permission to set the consent level for the [Kakao Account status change history] consent item through DevTalk.
- This permission is granted after a suitability review, so a specific usage scenario must be included when making a request.
- Once granted, set [Kakao Account status change details] as [Optional Consent] in [Kakao Login] > [Consent Items] on the app management page. Refer to Prerequisites.
CAEP and RISC category event information is provided only when the user has agreed to the [Kakao Account status change details] consent item. Services that are required to receive this information must set the [Kakao Account status change details] consent item to the [required consent] consent level.
Supported event types
The supported event types by category are as follows. If you select the category name, you can see detailed information about the events included in each category.
| Category | Description | Use Cases |
|---|---|---|
| OAUTH | Change event types related to the OAuth 2.0 protocol, including token issuance, revocation, and client state changes. Based on the OpenID Foundation's OAUTH specification. |
Get notified for Kakao Login users when linking or unlking an app, consenting to or withdrawing consent for scopes. |
| RISC | Change events related to anomalies in user Kakao Accounts.Based on the OpenID Foundation's RISC (Risk Incident Sharing and Coordination) specification. Important: Scope configuration and user consent are required. |
Get notified of abnormal account activities or account hijacking attempts. |
| CAEP | Change events related to credentials (tokens) and access rights issued to user Kakao Accounts.Based on the OpenID Foundation's CAEP (Continuous Access Evaluation Protocol) specification. Important: Scope configuration and user consent are required. |
Get notified when the authentication security level changes or the password is updated. |
| KAKAO | Events triggered by changes in user Kakao Account status information defined and provided by Kakao. | Get notified when profile information such as email or birthday is updated, or for Kakao-specific events not covered by OpenID standards. |
OAUTH
The OAUTH category includes change event types related to the OAuth 2.0 protocol.
| Event type | Triggering timing | Recommended actions |
|---|---|---|
Tokens Revokedhttps://schemas.openid.net/secevent/oauth/event-type/tokens-revoked |
Expiration of all tokens issued to a user via Kakao Login | Required: Terminate all active service sessions to protect the user account. |
User Linkedhttps://schemas.openid.net/secevent/oauth/event-type/user-linked |
User link to an app | Perform necessary actions for apps with [Auto-link with an app when logging in] set to [Disabled], such as completing user registration. |
User Unlinkedhttps://schemas.openid.net/secevent/oauth/event-type/user-unlinked |
User unlinks from an app | Unlink the Kakao Login from the app or delete the user account if Kakao Login is the only authentication method. Refer to Unlink webhook. |
User Scope Consenthttps://schemas.openid.net/secevent/oauth/event-type/user-scope-consent |
User consents to a scope | - |
User Scope Withdrawhttps://schemas.openid.net/secevent/oauth/event-type/user-scope-withdraw |
User withdraws consent for a scope | - |
RISC
The RISC category includes change events that notify of suspicious activities on user accounts. Scope configuration and user consent are required.
| Event type | Triggering timing | Recommended actions |
|---|---|---|
Account Credential Change Requiredhttps://schemas.openid.net/secevent/risc/event-type/account-credential-change-required |
User account password is changed | Review suspicious activities and decide on necessary follow-up actions. |
Account Disabledhttps://schemas.openid.net/secevent/risc/event-type/account-disabled |
User account is disabled (Example: Kakao Account protection, locking, or restriction) | Required: If the reason is hijacking, terminate all active sessions to protect the account. If bulk-account, analyze user activity and determine necessary measures. |
Account Enabledhttps://schemas.openid.net/secevent/risc/event-type/account-enabled |
User account is reactivated from dormant or hijacked state | Re-enable account recovery via Kakao Login and registered Kakao Account email. |
Account Purgedhttps://schemas.openid.net/secevent/risc/event-type/account-purged |
User account is deleted | Delete the user account or provide alternative login methods. |
Credential Compromisehttps://schemas.openid.net/secevent/risc/event-type/credential-compromise |
Credential compromise: Triggered when Kakao Account credentials are suspected of being compromised (Example: successful login from a suspicious new environment). |
Check for suspicious activities within the service and determine the necessary follow-up actions. |
Identifier Changedhttps://schemas.openid.net/secevent/risc/event-type/identifier-changed |
Identifier change: Triggered when the user's email address or phone number has been updated. |
Delete the old phone number or email address, and update the records with the new identifier. |
Identifier Recycledhttps://schemas.openid.net/secevent/risc/event-type/identifier-recycled |
Identifier reuse restriction: Triggered when a Kakao Account's email or phone number is reused by another user, causing the previous identifier to expire (Expired) or be suspended (Suspended). |
Prevent further use of the user's email or phone number in the service and directly collect new email or phone number information from the user. |
Sessions Revokedhttps://schemas.openid.net/secevent/risc/event-type/sessions-revoked |
All sessions terminated: Triggered after a password change, logging out from all previously used devices. |
Required: End all active sessions to protect the user's account. |
CAEP
The CAEP category includes change events related to user account credentials. Consent configuration and user consent are required.
| Event type | Triggering timing | Recommended actions |
|---|---|---|
Assurance Level Changehttps://schemas.openid.net/secevent/caep/event-type/assurance-level-change |
Changes in authentication security levels (Example: two-factor authentication setup) | Verify the user's compliance with the required security level for the service. If necessary, re-authenticate the user before granting service access. |
Credential Changehttps://schemas.openid.net/secevent/caep/event-type/credential-change |
Account credential update: Triggered when a password is reset or a Kakao certificate is reissued. | - |
KAKAO
The KAKAO category includes event types defined and provided by Kakao.
| Event type | Triggering timing | Recommended actions |
|---|---|---|
User Profile Changedhttps://schemas.kakao.com/platevent/kakao/event-type/user-profile-changed |
Changes to user Kakao Account information, notified only when user consent is given. | Call the Retrieve user information API, and then update the profile information with the new one. |
Security Event Token (SET)
The service receives a SET (Security Event Token) containing change event information of the Kakao Account through the POST method.
Below is an example of the request that is delivered to the webhook URL. Content-Type of the webhook request header is application/secevent+jwt, and the body is a SET value containing the change event information. SET is a JWT (JSON Web Token) type token and consists of the three parts.
POST /kakao/events HTTP/1.1
Host: callback.example.com
Content-Type: application/secevent+jwt
Accept: application/json
eyJraWQiOiI2NjVhYmVlYzExOGRkZmMyZDNiZjNlMmFkYWU3OT...
The SET is generated as a single string of three parts that are Base64-encoded and concatenated with the period (.). The contents can be verified by Base64-decoding after separating each part based on the period. After SET validation, the service can verify the payload contents to perform any necessary user account protection actions. Below is an example of a decoded SET header and payload.
{
"kid": "665abeec118ddfc2d3bf3e2adae799",
"typ": "secevent+jwt",
"alg": "RS256"
}
{
"aud": "${REST_API_KEY}",
"sub": "${USER_ID}",
"iss": "https://kauth.kakao.com",
"txm": "1ec82fca-ae18-471a-ab07-d94a2c2c0b12",
"toe": 1745460605,
"iat": 1745460605,
"jti": "8947a644-232c-46aa-a0cf-a628b2b8c8c8",
"events": {
"https://schemas.openid.net/secevent/oauth/event-type/user-linked": {
"subject": {
"sub": "701541",
"subject_type": "iss-sub",
"iss": "https://kauth.kakao.com"
}
}
}
}
SET configuration
| Category | Description |
|---|---|
| Header | SET specification |
| Payload | Change event information |
| Signature | A value signed by the Kakao Authentication Server (KAUTH) with the public key corresponding to kid in the header. |
Below are the details of the fields in the Header and Payload.
Header
| Name | Type | Description |
|---|---|---|
| alg | String |
The encryption applied to the SET, fixed to RS256 |
| typ | String |
Type of SET, fixed to secevent+jwt |
| kid | String |
Public key ID used to encrypt the SET Can be found through jwks_uri of Get metadata. |
Payload
| Name | Type | Description |
|---|---|---|
| aud | String |
The REST API key of the app receiving the SET. |
| sub | String |
Service user ID corresponding to the SET. |
| iss | String |
SET issuer. Fixed to https://kauth.kakao.com. |
| txm | String |
Unique identifier for the webhook event request |
| toe | Integer |
Event occurrence tim in Unix timestamp format (unit: seconds). |
| iat | Integer |
SET issuance time in Unix timestamp format (unit: seconds). |
| jti | String |
SET unique identification value. |
| events | Event |
Change event types and details. |
Event
| Name | Type | Description |
|---|---|---|
${SCHEMA} |
JSON |
Details by change event type. The key is Schema by Change event type.The value is different for each change event type. See Change event details below. |
Change event details
| Event Type | Name | Type | Description |
|---|---|---|---|
| Common | subject | Subject |
Change event details |
| OAuth > User Unlinked |
reason | String |
Reason for unlinking, one of the following:ACCOUNT_DELETE: The Kakao Account is deleted.FORCED_ACCOUNT_DELETE: The Kakao Account is deleted by the Customer Service or dormant state.INCOMPLETE_SIGN_UP: The Kakao Account is deleted because the user has not completed a signup.UNLINK_FROM_ADMIN: The Kakao Account is unlinked by admin.UNLINK_FROM_APPS: The Kakao Account is unlinked because a user selects [Disconnect] on [Manage connected services].REVOKE_ACCOUNT_SERVICE_TERMS: The user revoked the consent to the integrated service terms.UNLINK_FROM_SERVICE: The Kakao Account is unlinked from the service. |
| OAuth > User Scope Consent, User Scope Withdraw |
scope | String |
The consent items the user agreed to or revoked. A single string containing the ID of each consent item, separated by spaces. (Example: email birthday age_range) |
| RISC > Identifier Changed, Identifier Recycled |
new-value | String |
The phone number or email after the change |
| CAEP > Assurance Level Change |
current_level | String |
Current Kakao Account authentication levelnist-aal1: The second authentication is not set.nist-aal2: The second authentication is set. |
| change_direction | String |
The action type of the changeincrease: Increase authentication leveldecrease: Decrease authentication level |
|
| previous_level | String |
The previous Kakao Account authentication levelnist-aal1: The second authentication disablednist-aal2: The second authentication enabled |
|
| CAEP > Credential Change |
change_type | String |
The action type of the changeupdate: Change password or reissue Kakao certificate |
Subject
| Event Type | Name | Type | Description |
|---|---|---|---|
| Common | subject_type | String |
User Identifier Typeiss_sub: Service user IDphone: Phone numberemail: Email |
| iss | String |
SET issuer Fixed as https://kauth.kakao.com.Note: Not included in Identifier Changed and Identifier Recycled type change event information. |
|
| sub | String |
Service user ID corresponding to the SET Note: Not included in Identifier Changed and Identifier Recycled type change event information. |
|
| RISC > Identifier Changed, Identifier Recycled |
phone_number | String |
Existing phone number value that has been changed or disabled. |
String |
Existing email value that has been changed or disabled. |
Validate SET
The service must check and validate the contents of the SET before performing user account protection actions based on change event information. You can check and verify the SET contents in the following order:
- Separate the header, payload, and signature based on the period (.).
- Decode the payload in Base64.
- Verify that the
issvalue in the payload matcheshttps://kauth.kakao.com. - Verify that the
audvalue in the payload matches the service app's REST API key. - Verify the signature
Signature verification proceeds in the following order.
- Decode the header in Base64.
- Request OIDC: Get public key to get the list of public keys used by the Kakao authentication server for signing.
- Check the public key value corresponding to the
kidof the header in the public key list.- Caching the public key for a certain period is recommended, and note that requests may be blocked if they are too frequent.
- Verify the signature with the public key using a library that supports JWT signature verification.
- Note: OpenID Foundation, jwt.io
- When implementing signature verification directly without using a library, the signature verification process can be performed according to the RFC7515 specification.
Validation success response
If the SET receiving server receives a webhook request via the webhook URL and the SET validation is successful, you should respond with the HTTP response code 202 Accepted with no response body. See the example below.
HTTP/1.1 202 Accepted
Validation failure response
If the SET receiving server fails to validate the SET after receiving the webhook, you must respond within 3 seconds using the following format:
- HTTP status code:
400 Bad Request - Header:
Content-Type:application/json - Body: In JSON format, including the error code (
err) and reason (description) as specified in the RFC8935 standard.
HTTP/1.1 400 Bad Request
Content-Type: application/json
{
"err": "invalid_key",
"description": "Key ID 12345 has been revoked."
}
Failure response error codes
| Error Code | Description |
|---|---|
| invalid_request | When the delivered SET does not comply with the JWT specification. |
| invalid_key | When failed to decrypt the delivered SET with Kakao's public key. |
| invalid_issuer | If the issuer of the delivered SET is not Kakao. |
| invalid_audience | If the aud value of the delivered SET does not match the service app ID. |
Get metadata
Basic information
| Method | URL | Authentication |
|---|---|---|
GET |
https://kauth.kakao.com/.well-known/ssf-configuration | - |
You can retrieve the Account status change webhook specification.
Response
| Name | Type | Description | Required |
|---|---|---|---|
| issuer | String |
SET issuer Fixed to https://kauth.kakao.com |
O |
| jwks_uri | String |
The URI to retrieve the public key used for SET encryption A public key is required for SET verification |
O |
| delivery_methods_supported | String |
Supported SSE event delivery methods Only push is supported |
O |
Sample
Request
curl -X GET https://kauth.kakao.com/.well-known/ssf-configuration
Response
HTTP/1.1 200
{
"issuer": "https://kauth.kakao.com",
"jwks_uri": "https://kauth.kakao.com/.well-known/jwks.json",
"delivery_methods_supported": "http://schemas.openid.net/secevent/risc/delivery-method/push"
}
Test
You can try sending webooks to see if webhooks work normally in [Tools] > [Webhook Test].
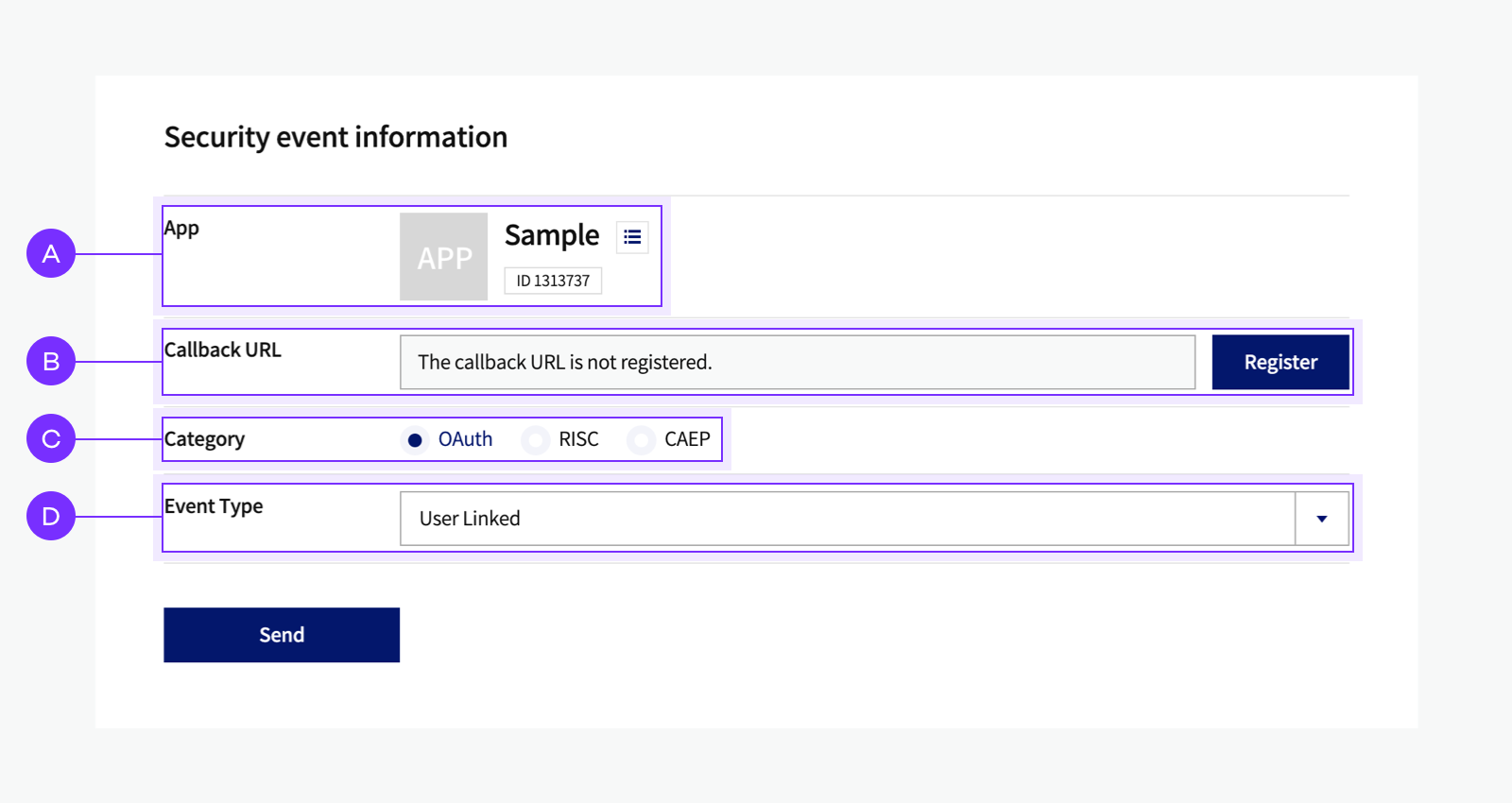
🅐 App: Select an app to test. 🅑 Webhook URL: Displays the webhook URL you set in Account status change webhook. If you have not set, register a webhook URL first. 🅒 Category: Select a change event category. All categories can be selected for testing. 🅓 Event type: Select a change event type to send. Note that RISC and CAEP categories typically require permissions but are available for testing. 🅔 Kakao Account: Select a team member registered with the app to send the event. The selected account must be [link] to the app to trigger events. 🅕 Parameters: For some categories, you need to set parameters. See the table below for details.
| Category | Event Type | Parameter |
|---|---|---|
| OAuth | User Unlinked | reason: Select the reason for the user unlinking from the app. |
| OAuth | User ServiceTerms Consent | scope: Select the scopes to receive webhooks when a user consents to the scopes. |
| OAuth | User ServiceTerms Withdraw | scope: Select the scopes to receive webhooks when a user withdraws the scopes. |
| OAuth | Tokens Revoked | reason: Specify who expired the token, either issuer or user. |
| RISC | Account Disabled | reason: Select the reason for disabling the Kakao Account. |
| RISC | Identifier Changed | subject_type: Choose the identifier type, either phone or email.new_value: Enter the new phone number or email. |
| CAEP | Assurance Level Change | previous_value: Select the Kakao Account authentication level before the change.new_value: Select the authentication level after the change, either nist-aal1 (no two-factor authentication) or nist-aal2 (two-factor authentication enabled). |
| KAKAO | User Profile Changed | profile: Specify the type of user information to trigger change events.(Example: account_email birthday age_range) |
After selecting [Send], the test information appears at the bottom of the page, as shown below.
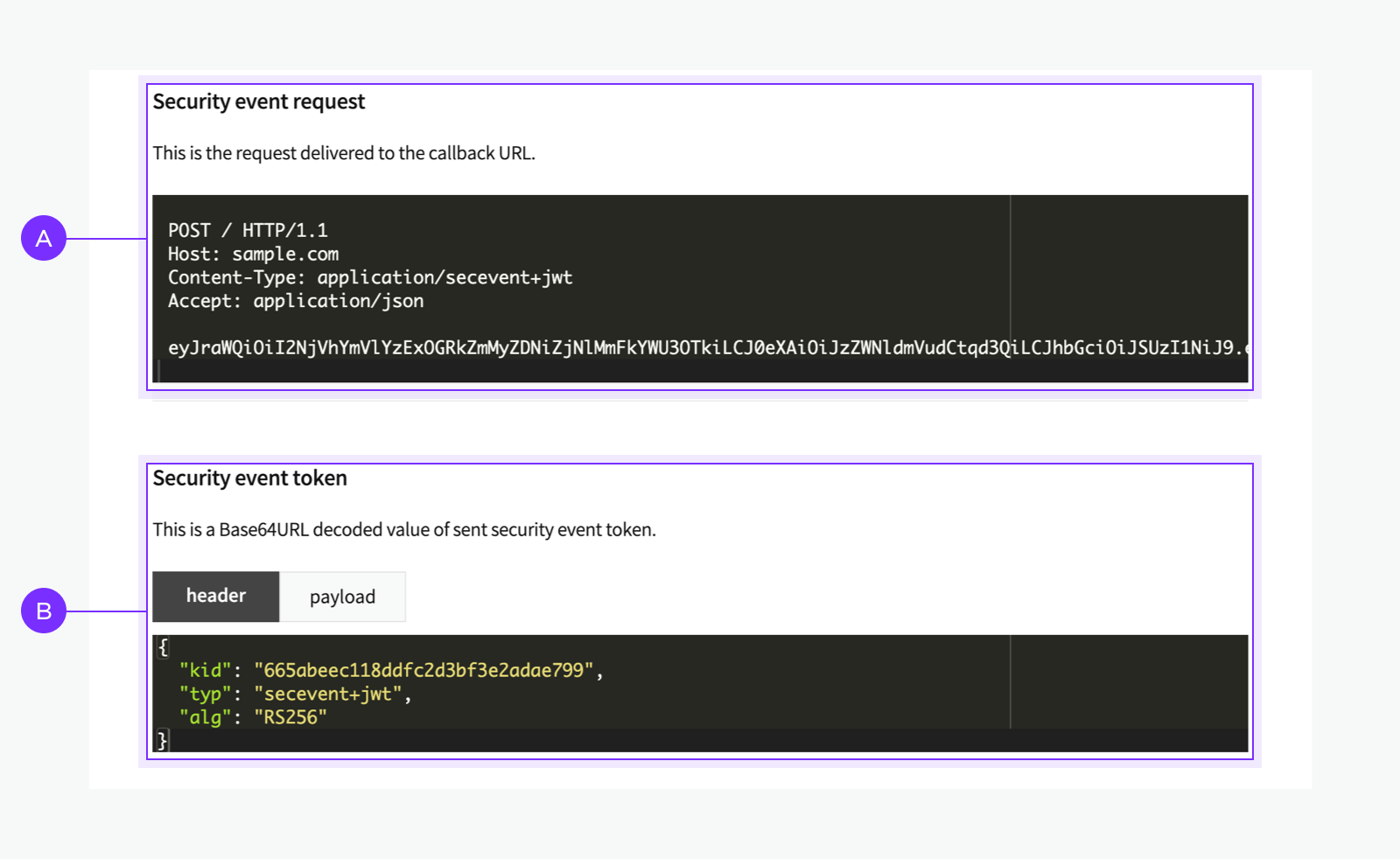
🅐 Webhook request: Full text of the test request. Host and URL are excluded in the output when the webhook URL is not set.
🅑 Security event Token: The decoded value of the SET contained in the request is in 🅐. The header and payload are output respectively. Refer to this when debugging.